News
What is Phishing? Case Study and how to identify actual phishing emails
The Internet environment has many bad guys looking for ways to steal information, personal data, even money of others. One of the common tricks of hackers is using phishing emails. Therefore, take a few minutes to see how to identify phishing emails to stay away from these dangerous traps.
What is Phishing?
Phishing is a large-scale cyber attack, Hacker will use Email to disguise itself as a message from a reputable address. The purpose of this is to trick the email recipient into believing that the message received is what they need. For example, the body of the message is a request from the bank they are using, or a note from a colleague in the company. The message asks the reader to click on a link or download an attachment that is actually malware. Or you may be asked to enter confidential information into a phishing Web site, which the hacker will gain access to.
These phishing attacks can be delivered to a large number of Email recipients. And I'm sure that if only a small number of people are trapped, the attack will be successful, the hackers will get a lot of benefits from it.
Hackers often trick individuals into providing sensitive data such as personally identifiable information, bank and credit card details, and passwords. This information will then be used to access important accounts and can lead to identity theft and unforeseen financial loss. Therefore, each of us needs to know how to identify phishing emails to minimize these risks.
What is Spear Phishing?
This is one of the not uncommon types of Phishing. Spear Phishing is a form of fraud aimed at a specific individual, organization or business. This form is also often used by attackers through phishing emails. Usually, Hacker will impersonate a reputable individual, department or organization to send Email and trick you into revealing information.
For example, an attacker will send Emails to a bunch of users. They will impersonate the IT department and ask you to re-enter login information on a certain Web. Or another example is a cybercriminal posing as a human resources department, attaching new terms and benefits packages to stimulate you to Click to open. While Spear Phishing usually aims to steal usage data for malicious purposes, scammers may also intend to install spyware on your device.
Why is Phishing a threat?
As far as I know, even professionals can fall victim to Phishing. Moreover, this recognition of phishing email is not easy. This makes Phishing really an unpredictable threat. Intel says that up to 95% of attacks on corporate networks are the result of Spear Phishing.
Research shows that up to 94% of employees can't tell the difference between Phishing Email and Real Email. Among them, 11% of these users Click on the attachments in the Phishing Email. Therefore, their computers are infected with malware, or may have information stolen.
The research of Kapost also revealed a worrying situation:
96% of experts globally were unable to find the exact difference between a Phishing Email and a Real Email.
Anyone can be at risk of becoming a victim of Phishing, including highly security-conscious users.
As can be seen, the danger from Spear Phishing could not be taken lightly. Fake Emails sometimes show clues like attachments with .exe extensions, typos and so on. But in reality it won't be easy for you or me to distinguish between secure emails. and fake email. However, the rate of email fraud will be reduced if we have security knowledge.
It's easy to create a fake Email

Scammers can create impersonation emails very easily.
To bypass the ways to identify phishing emails, scammers will of course also have their own ways to create fake emails. These methods are not difficult at all. I will show you how to create a fake Email. Thereby, you can understand that these Phishing Emails can be mass generated easily and this is not positive for users at all.
Hackers can completely create email quickly with SMTP tool easy to download from the Internet. You can create one domain and multiple accounts either directly from your Outlook account or from the server.
After creating Emails, you can send them instantly from Outlook. The fact that you can easily mass-produce these emails means that hackers can do it too. Hackers can create and send you fake Emails to steal your personal information. This shows that you can impersonate anyone and vice versa. However, I also want to inform you of the good news that we still have a solution to deal with. For example, the digital certificate Digital Certificate, which I will analyze in more detail below.
What is Digital Certificate?
A Digital Certificate is an electronic credential that binds the identity of the certificate holder to a pair of electronic encryption keys. It can be used to encrypt and sign digital information. The main purpose of a Digital Certificate is to verify that a message sender is the original owner, confirming the correct identity. Digital Certificates are issued by certificate authorities (Certificate Authorities - CA for short). A process called Vetting will be required for the Certificate Authorities to identify who you are. The Digital Certificate will allow you to electronically encrypt and sign an Email.
CA has multiple levels of censorship. Certificate Authorities in its simplest form will only check the Email if it is owned by the applicant. Certificate Authorities at the second level will perform identity checks. Certificate Authorities at higher levels will do things related to verifying the physical, corporate location of that individual.
Using digital signature in Email

Digital signature proves the origin of the Email.
Considering digital signatures in emails is one of the effective ways of identifying phishing emails. The sender's identity will be verified, clearly displayed in the Email. You can rely on digital signatures to confirm that the Email you receive is from a safe, legitimate source. In summary, digital signatures in Email have the following characteristics:
Prove the origin of the email sent to.
Ensure message integrity. When you open an incoming message, your Email application checks the content of the message. The purpose is to see if it matches the contents of the digital signature. This check will fail if there is the slightest change from the original document. Thanks to that, you can see the anomaly more easily.
Digital signatures are undeniable. An electronic signature identifies and proves the identity of an individual or organization that has signed and sent an Email. Therefore, the sender will not be able to deny that they have signed on the Email.
A sad example of a victim of Phishing
To further demonstrate the dangers of Phishing, I will tell a true story, a sad example of a victim of Phishing. A few years ago, a company was hacked, almost every data file was encrypted and stolen. The attacker demanded a ransom of 700 USD and the company was forced to follow the request to get the data back.
The company also hired a security expert to help. This expert said, Hacker sends Email with an attachment named My Resume. It is very easy for the recipient to open this file, especially when the company is in need of human resources. At this time, Ransomware infiltrates the system and encrypts the data.
How to detect fake email
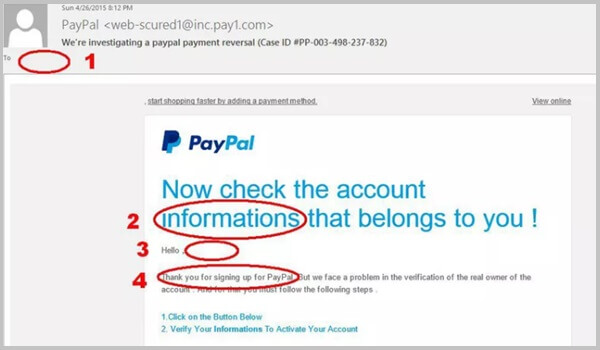
Phishing emails often have signs of spelling, grammar, ...
I will guide you through some how to identify phishing emails synthesized by experts:
One of the signs of Phishing is spelling and grammar mistakes in Email. Large companies will have specialized departments to compose content, communicate via Email and rarely make these mistakes.
Missing recipient's name in Email greeting.
The subject line, email content has attractive, eye-catching or unusually attention-grabbing offers. For example, announcing you won an iPhone, won the lottery,...
A favorite tactic of cybercriminals is to ask you to act quickly, Click the link now because the super deals are only available for a limited time.
When you come across this Email from an unknown address, I think it's best to ignore them.
With emails with strange attachments, you should not open them either. They often contain Ransomware or other viruses.
How to avoid Email Phishing
A more sophisticated trick of email phishing is to worry you with a warning about stolen information. Then it asks you to download anti-virus software according to the attached file, or it will provide an easy fix just by clicking the link. Be wise not to be deceived.
I recommend that you enable your Virus scanner. Then you open your browser, go to the company's Web site, log in for any strange signs. To be more sure, you can change the password.
In addition, the content of Phishing Emails will often have spelling and grammatical errors. Because most of them are not written by native speakers, are automatically mass generated,... As for reputable organizations, as I mentioned above, their Email content will be prepared by experts. . Therefore, it will be very difficult to make such basic errors. If you see a typo, to be on the safe side I think you should not open, Click on the files, Link in this Email.
More than that, you should increase the security of your browser. You can use free browser add-ons such as Web of Trust and McAfee SiteAdvisor to be alerted if the Web site you are about to visit appears unsafe. Remember, never give out passwords, personal financial information, even the bank does not ask you for this information.
5 myths about Phishing
A lot of myths about Phishing can make you subjective in preventing the risk of being hacked. I will list 5 myths about Phishing so you can learn from it and better protect your personal information.
Underestimated the danger of Phishing
Too dependent on spam filters
Is it possible to block email phishing with domain authentication?
I don't need to take action to protect personal and company information from Email Phishing
Underestimated the danger of Phishing
I know that, in many cases, due to disregarding fraudulent emails, there are undesired consequences. Do not be too subjective with your ability to recognize email impersonation. Because Hackers are also constantly looking for ways to trick users. You are not always knowledgeable enough to know that you are being cheated.
Too dependent on spam filters

Spam filters are not as universal and perfect as many of you think.
Spam mail filter is not perfect, will not filter 100% of impersonation mail, any Phishing attack. A "high-handed" attacker will still have a way to "circumvent the law" to pass the filter. So I think each of us has to be a premium filter for our own inbox. Don't carelessly click on every email that comes in, take the time to read it and summarize it with the how to identify Phishing Emails you know. appear in your mailbox.
Is it possible to block email phishing with domain authentication?
This is another misconception of many users. Hackers spreading Email Spam will also be very professional. Attackers can completely invest in Email domain names themselves, or use tricks to bypass this gate easily.
Block Email Phishing by Detecting Vulnerabilities in URLs
Vulnerability in the URL is a sign to recognize the abnormality of Email. However, this test is not entirely correct. Many large companies still use long URLs, Redirect URLs, use raw IP addresses in Email. The attacker fully understood and took advantage of this vulnerability.
I don't need to take action to protect personal and company information from Email Phishing
This myth can cause very bad risks and consequences. Do not be passive in the protection of personal data because you can have your finances, personal information, even top secret company data stolen.
I hope through the article you will have a better understanding of how dangerous Phishing is. Be equipped with Email protection system and stay up to date with the latest how to identify phishing emails .
Thiết kế web theo chuẩn mobile
06/03/2022Hiện nay Google đã chính thức thay đổi thuâtj toán tìm kiếm trên các thiết bị di động. Thuật toán Mobile Friendly sẽ ảnh hưởng đáng kể đến việc sắp xếp thứ hạng các website trên...
Thiết kế web Tp Hồ Chí Minh giá rẻ?
06/03/2022Bạn đang muốn lựa chọn một đơn vị thiết kế web Tp Hồ Chí Minh giá rẻ? Bạn thấy rất nhiều quảng cáo thiết kế web giá rẻ, hấp dẫn mà chưa biết ra sao?
Thiết kế web doanh nghiệp tại Tp Hồ Chí Minh và Toàn Quốc
06/03/2022Đầu những năm 2000, số lượng các doanh nghiệp có website còn thấp, giờ đây việc doanh nghiệp có website đã trở thành một nhu cầu cơ bản...
Thiết kế web công ty
06/03/2022Bạn đang muốn quảng bá hình ảnh doanh nghiệp và sản phẩm, dịch vụ với các đối tác trong và ngoài nước? Bạn muốn nâng cao doanh số bán hàng và mở rộng thị trường
Thiết kế web tại Tp Hồ Chí Minh
06/03/2022Bạn đang tìm một công ty thiết kế website tại Tp Hồ Chí Minh chuyên nghiệp? Long Thịnh là công ty hàng đầu trong lĩnh vực thiết kế website chuyên nghiệp
Quy trình và thời gian thiết kế web tại Long Thịnh
06/03/2022Để làm ra một website chất lượng, đòi hỏi một quy trình chuyên nghiệp và có rất nhiều công đoạn cũng như có sự tham gia của nhiều nhân viên chuyên trách
Tiêu chí thiết kế website chuẩn SEO nâng cao
06/03/2022Làm thế nào để tối ưu trang web thân thiện với công cụ tìm kiếm? Các chuyên gia hàng đầu trong lĩnh vực Marketing trực tuyến đã nghiên cứu các tiêu chí website chuẩn SEO
Sau khi thiết kế, bạn cần phát triển website như thế nào?
06/03/2022Đa phần khách hàng sau khi thiết kế website xong thì website chỉ được sử dụng như là nơi để đăng tải giới thiệu một số sản phẩm mà thiếu đi sự kết nối với một số trang
6 tiêu chí quan trọng đánh giá 1 website chất lượng
06/03/2022Website của bạn có thực sự hiệu quả khi hoạt động trên Internet hay không. Những thiếu xót của bạn khi đầu tư vào website. Hãy tham khảo 4 tiêu chí sau để đánh giá lại web
Tại sao phải sử dụng Email theo tên miền?
06/03/2022Quản lý tập trung với tên miền riêng tạo sự tin cậy cho đối tác, quản lý nội dung email, tích hợp với giải pháp văn phòng, dung lượng lớn và chống spam mail hiệu quả.